Would you recognize the sound of a bank account being drained?
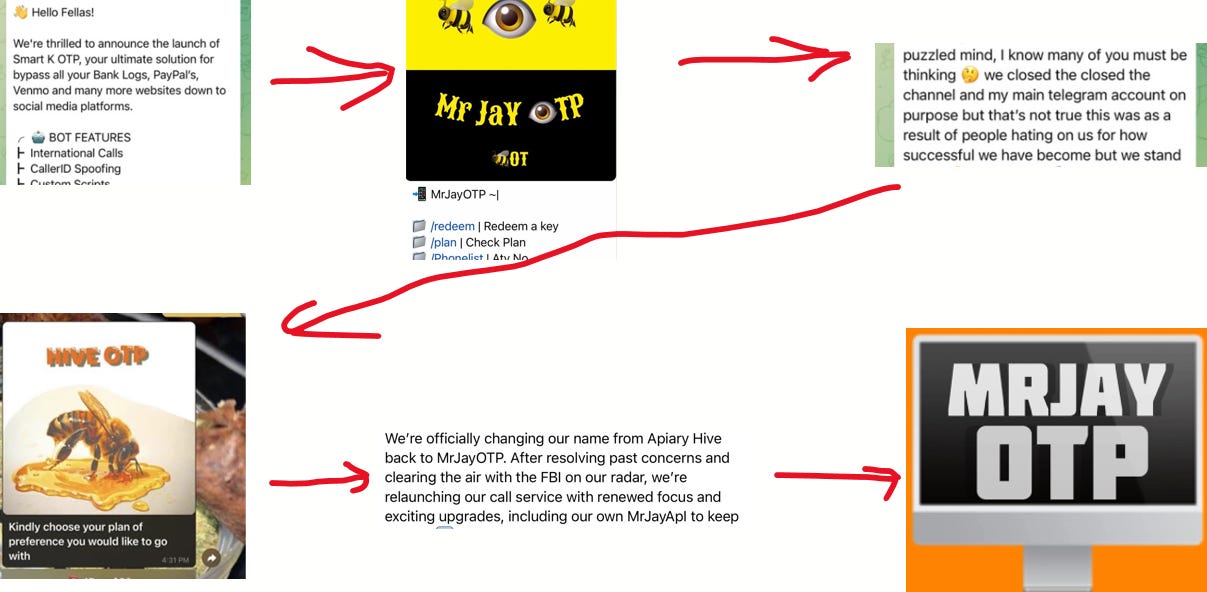
Today we publish the first public findings on MrJayOTP.
Today we publish the first public findings on MrJayOTP, an operational “OTP bot” that turns phone calls into a high-velocity tool for harvesting one-time passcodes, all packaged in a SaaS solution with slick marketing. We’re also publishing an audio sample so defenders can hear how this works. This post walks through what we observed, why it matters, and what security teams should do now.
What is MrJayOTP?
At a high level, MrJayOTP is a voice-first social-engineering platform packaged as a subscription-based service. It provides a single, integrated workflow for running scripted voice calls, compromising one-time passcodes in real time, and surfacing those codes to attackers who can then complete an authentication or transaction.
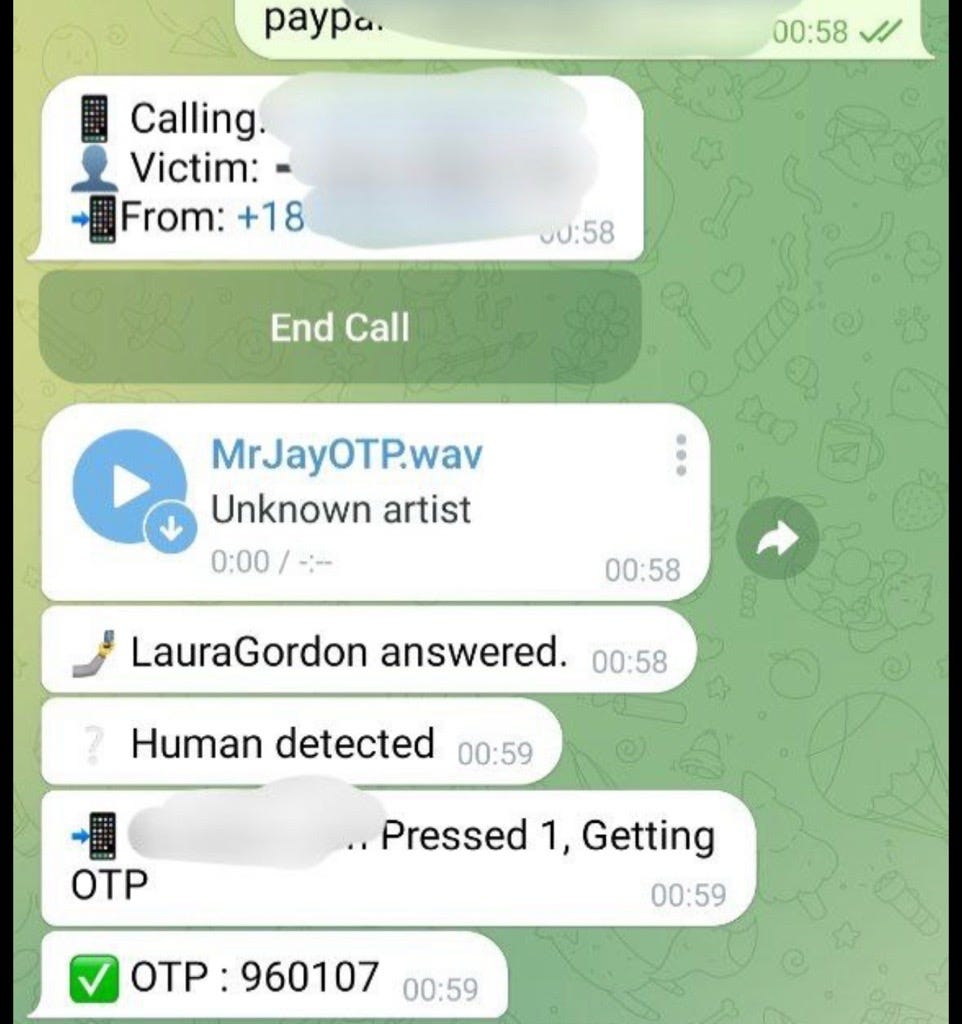
An attacker begins a process, such as account takeover or a money transfer, and hits an MFA request. Attack foiled, right? No. They send the target with the name of the service over to MrJayOTP, and with one click, the bot makes a phone call and obtains the MFA from the victim via social engineering.
The components of this attack aren’t new. The attacker could attempt to impersonate the bank themselves. Or they could grab some code off of GitHub, hook it into a compromised corporate 3CX phone switch (PBX), hook it into a voice generator AI, and run it on a local machine. In fact, the current iteration of MrJayOTP itself is at least number four in a product line from this developer dating back to 2021. But by packaging all of the needed components into a SaaS product, the barrier to entry for fraud becomes that much lower.
Several characteristics make the product noteworthy:
Voice-based man-in-the-middle (MiTM): The platform’s primary vector is a phone call that targets the human step in multi-factor authentication. It is not malware, it is not a network interception tool, and it is not a browser prompt. Instead, it persuades the target — via audio — to reveal or enter a code.
OTP-agnostic capture: Captured codes may be delivered via SMS, generated by an authenticator app, or come from any other source. The platform exploits the human act of reading or entering the code rather than breaking the authentication algorithm.
Real-time DTMF/read-back capture: The system captures target keystrokes and read-back codes during the call and displays them immediately on the attacker’s screen, enabling real-time use.
Turnkey workflow and scale: MrJayOTP bundles caller-ID spoofing, multilingual synthetic voices, a growing list of pre-built modes (banks, brokerages, carriers, exchanges, payment gateways, cloud services, etc.), customizable scripts, and automation. That integration lowers the operational skill bar and enables higher-volume campaigns.
Why this is dangerous
Security teams are staring to understand that OTP is a weaker MFA factor. Platforms like MrJayOTP change the risk calculus in several important ways:
Caller-ID spoofing, paired with authoritative scripts and a sense of urgency, can make a call sound legitimate.
Human-centered bypass: The attack bypasses authentication by targeting a person. Even authenticator app codes and platform-based prompts are vulnerable if the target reads them aloud or types them on the phone keypad.
Scale and efficiency: By combining multiple features into one panel, the platform enables less sophisticated operators to execute high-volume attacks that previously required more skill and tool-chaining.
Defenders’ checklist
The following mitigations are practical and intentionally high-level.
Move to phishing-resistant MFA where feasible. Promote FIDO2/security keys and platform-bound asymmetric credentials over SMS or other OTP-based systems.
Monitor call and authentication telemetry together. Correlate unusual call patterns with authentication attempts — e.g., a spike in inbound calls that precede high-value auth attempts, or abnormal DTMF activity.
Harden call-center and customer workflows. Train agents to avoid asking for OTPs, implement escalation paths for suspicious requests, and require out-of-band verification for high-value changes.
Improve user awareness. Educate users and team members on how this type of attack works. Click below to listen to a recording of a MrJayOTP bot request targeting John’s PayPal account.
Back-end notes:
Telegram as a telemetry channel: During analysis we observed that the platform streams metadata — including target phone numbers and the services being impersonated — to a Telegram channel under admin control. This stream functions as a real-time activity log: it shows which numbers are being targeted and what brand or service the operator is portraying during each call.
Azure AI: The bot hooks into Azure AI to generate the speech:
Upstream services: The bot relies on an upstream provider for routing voice calls. Below is a screenshot from the developer’s device making payment for a route via cryptocurrency:
We can use that data to see payment flow. The upstream provider sends those payments to a Binance wallet:
History: MrJayOTP has undergone a few iterations dating back to 2021:
Closing thoughts
Tools like MrJayOTP demonstrate a progression toward automation and AI on the social side of fraud. The controls that once worked at low scale can become brittle when paired with scripted persuasion and real-time capture. The best defenses combine phishing-resistant authentication, telemetry-driven detections, and ongoing user awareness training.






Really clear description of this threat, Travis. Great work.